Introduction
In the era of cloud computing, one of the most common architectural patterns involves combining Infrastructure-as-a-Service (IaaS) components, like virtual machines, with Platform-as-a-Service (PaaS) offerings, such as managed databases or storage accounts. While this hybrid approach offers immense power and flexibility, it introduces a critical security challenge: How do you allow your private virtual machines to communicate with PaaS services without exposing those services to the public internet?
By default, most Azure PaaS services are accessed via public endpoints. This is convenient but can be a non-starter for organizations with strict security and compliance requirements. A publicly accessible database, even one protected by a strong password, presents a larger attack surface than one that is completely isolated from the internet.
This is the problem our architecture solves. It demonstrates and compares two fundamental Azure networking features designed to bridge the gap between your private IaaS network and Azure’s PaaS offerings securely: Azure Service Endpoints and Azure Private Endpoints. Understanding the nuances between these two options is crucial for any cloud architect or engineer aiming to build a secure, efficient, and robust cloud environment. This post will break down the architecture, compare the design choices, and guide you on when to use each approach.
Architecture Overview
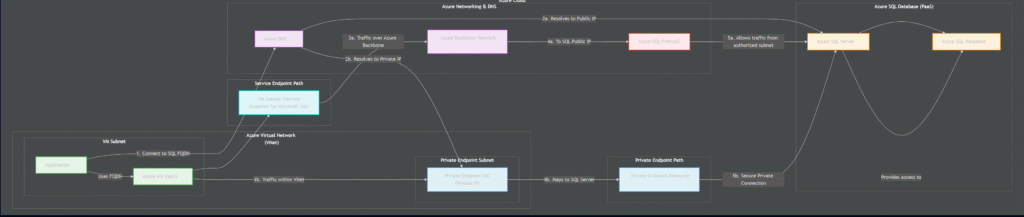
At a high level, the diagram illustrates a common scenario: an application running on an Azure Virtual Machine (IaaS) needs to connect to an Azure SQL Database (PaaS). The core of the architecture is to showcase two distinct, secure pathways for this connection, moving from a public-by-default model to a truly private one.
The data flow for both patterns begins at the app running on the vm. This application uses a standard connection string, which points to the Fully Qualified Domain Name (FQDN) of the Azure SQL Server. From here, the path diverges:
- The Service Endpoint Path (Top Route): In this model, the VM’s subnet is configured with a Service Endpoint for
Microsoft.Sql. When the application tries to connect, Azure networking intelligently routes the traffic. Instead of going over the public internet, the connection travels over the highly optimized Azure backbone network directly to the PaaS service’s public IP address. The Azure SQL Server’s firewall is configured to accept traffic only from this specific source subnet, effectively creating a secure, private tunnel over Azure’s infrastructure. - The Private Endpoint Path (Bottom Route): This model takes a different approach to achieve even greater isolation. A Private Endpoint is created, which is essentially a network interface card (NIC) that lives inside the VM’s own virtual network (VNet) and has a private IP address from the VNet’s address range. This NIC is logically mapped to the specific Azure SQL Server instance. When the application resolves the database FQDN, Azure DNS directs it to this private IP address. The traffic flows from the VM to the private endpoint NIC entirely within the private VNet, never touching a public network path.
Component Breakdown
Let’s dissect the individual components and their roles in this architecture.
IaaS Compute (Virtual Machine)
- VM: This represents any IaaS compute resource running within an Azure Virtual Network. While depicted as a single VM, this could be a scale set, a Kubernetes cluster, or any other service that resides within a VNet.
- App: This is the application layer that requires database access. Its
conn.string(connection string) is the key that initiates the entire process, typically containing the server’s FQDN (e.g.,your-sql-server.database.windows.net).
PaaS Data Store (Azure SQL Database)
- Azure SQL Server & SQL DB: This is our target PaaS service. It’s a fully managed relational database service provided by Microsoft. By default, it is provisioned with a public endpoint and secured by firewall rules and credentials. Our goal is to restrict access to it from our private network only. The connection is made to the server’s FQDN on the standard port
1433.
Azure Service Endpoint
A Service Endpoint is a feature configured at the subnet level within a Virtual Network. Its purpose is to extend your VNet’s private address space and identity to specific Azure services.
- How it works: When enabled for a service (like Azure SQL or Azure Storage), it adds a special route to the subnet. Any traffic destined for that Azure service type is automatically redirected from its default path (the internet) to the Azure backbone network.
- Security Model: The security is enforced on the PaaS side. You configure the Azure SQL firewall to allow access from the “virtual network” source, selecting the specific VNet and subnet. The PaaS service validates that the traffic originates from an authorized subnet before accepting the connection.
Azure Private Endpoint
A Private Endpoint is a more advanced feature that provides true private connectivity. It is a network resource in its own right.
- How it works: It projects a PaaS service directly into your VNet by creating a dedicated network interface (
nic) for it. This NIC gets a private IP address from your subnet’s IP range. Azure’s Private DNS service is then used to resolve the PaaS service’s public FQDN to this new private IP address for any requests originating from within the VNet. - Security Model: The connection is inherently private. The traffic is simply routed from one private IP (the VM) to another private IP (the private endpoint) within your network. You can even apply Network Security Groups (NSGs) to the subnet containing the private endpoint for fine-grained traffic filtering, a capability not available with Service Endpoints.
Key Design Decisions
The choice between a Service Endpoint and a Private Endpoint is a critical design decision with significant implications for security, complexity, and cost.
Why Choose Service Endpoints? Simplicity and Ease of Use.
Service Endpoints are the simpler of the two options. Enabling them is often as easy as checking a box in the subnet’s configuration.
- Best for: Scenarios where you need a quick and straightforward way to secure traffic from an entire subnet to a class of PaaS services (e.g., allow all VMs in the “app-subnet” to talk to any Azure SQL database you authorize). It’s a great initial step away from allowing all public traffic.
- Limitations: The PaaS service endpoint remains public. While secured, it’s still technically on a public IP, which may not satisfy stringent compliance rules. Furthermore, it provides access at the service level, not the specific resource instance, which can lead to data exfiltration risks if not carefully managed.
Why Choose Private Endpoints? Ultimate Security and Flexibility.
Private Endpoints are the modern standard and recommended best practice for most use cases, providing superior security and connectivity options.
- Granular, Resource-Specific Security: A Private Endpoint maps to a specific instance of a PaaS service (e.g.,
your-sql-server, not all of Azure SQL). This eliminates the risk of data exfiltration, as a compromised VM cannot use the private connection to reach a different, unauthorized SQL server. - True Network Isolation: With a Private Endpoint, you can completely disable the public endpoint of the PaaS service. This means the resource is truly dark to the public internet, offering the highest level of network isolation.
- Extended Connectivity: As the diagram notes, Private Endpoints are fully routable within your private network ecosystem. This means they work seamlessly across:
- Cross-Region VNet Peering: Connect to a PaaS service in another region.
- Hybrid Connections: Access PaaS services from your on-premises data center over a VPN or ExpressRoute connection.
- Inter-Tenant Scenarios: Securely connect to a partner’s PaaS service in a different Azure AD tenant.
Service Endpoints cannot support these advanced hybrid and cross-network scenarios.
Scalability & Security Considerations
Scalability
Both solutions are built on the hyper-scale Azure fabric and do not pose a bottleneck to the scalability of your application or database. The PaaS service itself (Azure SQL) can be scaled independently based on its performance tier.
- Management at Scale: For large environments with many VNets and PaaS services, managing Private Endpoints requires a robust DNS strategy, typically involving Azure Private DNS Zones. While more complex than Service Endpoints, this centralized DNS management provides better control and visibility. Service Endpoints are simpler as the configuration is decentralized to each subnet.
Security
This is where the distinction is most critical.
- Service Endpoints Security:
- Protection: Secures traffic between your VNet and Azure services, ensuring it stays on the Microsoft backbone.
- Weakness (Data Exfiltration): The primary security concern is the potential for data exfiltration. If a malicious actor gains control of a VM in a Service Endpoint-enabled subnet, they could potentially connect to another Azure SQL database outside of your control, as long as that database’s firewall was open. The protection is at the source (subnet), not the specific destination.
- Private Endpoints Security:
- Protection: Provides true private connectivity, effectively making the PaaS service a first-class citizen of your VNet.
- Strength (Data Exfiltration Prevention): This model completely mitigates the data exfiltration risk seen with Service Endpoints. The private DNS ensures that the FQDN resolves only to the private IP of your authorized SQL server. Any attempt to reach another server would fail at the DNS level or be blocked by network routing.
- Strength (Defense in Depth): The ability to apply NSGs to the private endpoint’s subnet allows for an additional layer of security, enabling you to control precisely which resources (e.g., which specific VMs) can communicate with the PaaS service.
Conclusion
The architecture presented highlights a fundamental evolution in cloud networking security. While Service Endpoints offer a valuable and simple method for securing PaaS traffic from a VNet, they represent an older, less granular model. They are a solid choice for less complex environments or as an initial security hardening step.
However, for any new or business-critical application, Private Endpoints are the definitive best practice. They provide unparalleled network isolation, mitigate sophisticated threats like data exfiltration, and offer the flexibility required for modern hybrid and multi-region cloud architectures. By bringing your PaaS services directly into your private network, you can build a zero-trust environment that meets the highest standards of security and compliance.
As you design your Azure solutions, carefully consider your connectivity and security requirements. Choosing the right VNet integration pattern is not just a technical detail—it’s a foundational decision that will define the security posture and future-readiness of your entire cloud platform.